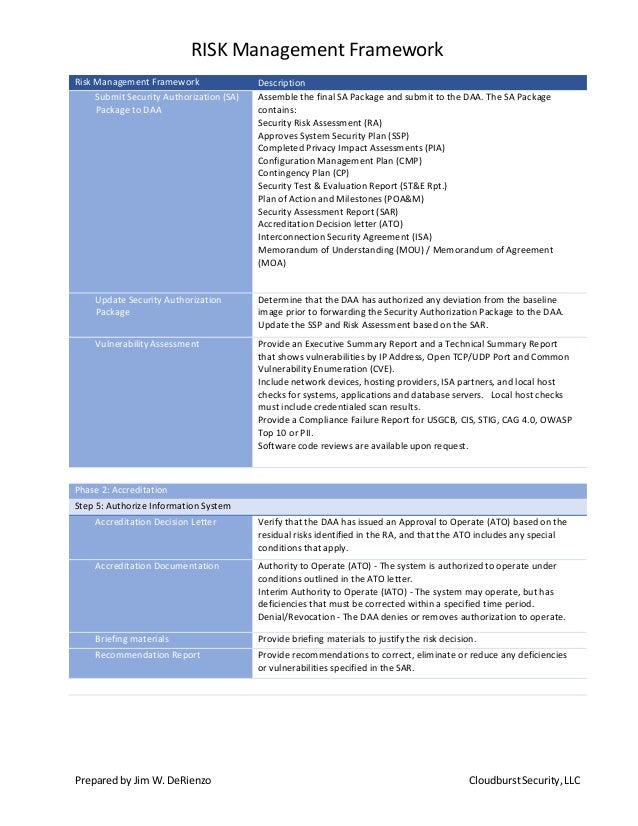
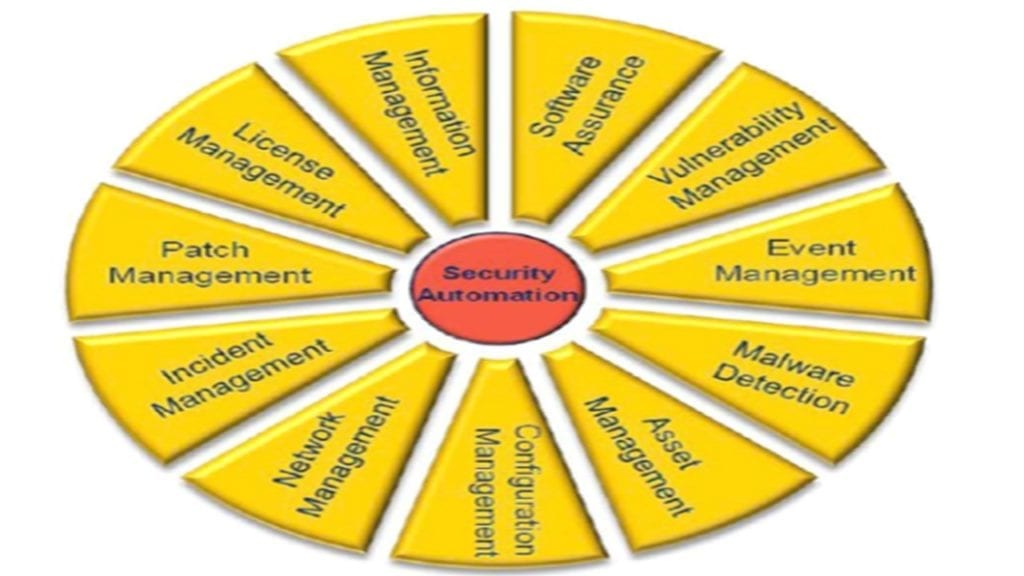
Nist Continuous Monitoring Plan Template
Nist Continuous Monitoring Plan Template - Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web after reviewing more than a year’s worth of community feedback, nist has released a draft of nist releases. Web 805 in this template, the action plan includes rows for the priority of each action item, a description 806 of the action. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities,. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and.
Nist information system contingency plan templates for high, moderate, and low. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web october 01, 2020. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through. Web abstract this publication describes an example methodology for assessing an organization's information. Web planning and transition purposes, federal agencies may wish to closely follow the development of these new. Web assessing information security continuous monitoring (iscm) programs:
Continuous monitoring strategy_guide_072712
Web 805 in this template, the action plan includes rows for the priority of each action item, a description 806 of the action. Developing an iscm program assessment kelley. Web abstract this publication describes an example methodology for assessing an organization's information. Web october 01, 2020. Web on c&a activities what is continuous monitoring? Developing.
NIST Cybersecurity Framework Cybersecurity framework, Cyber security
Web assessing information security continuous monitoring (iscm) programs: Web nistir 8212, an information security continuous monitoring program assessment, provides an operational. Web abstract this publication describes an approach for the development of information security continuous. Nist information system contingency plan templates for high, moderate, and low. Web on c&a activities what is continuous monitoring? Web.
NIST SP 800137 Information security continuous monitoring (ISCM)
Web abstract this publication describes an example methodology for assessing an organization’s information. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities,. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web continuous monitoring (iscm) program. Developing an.
Risk Management DANIEL PRATT
Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web abstract this publication describes an example methodology for assessing an organization's information. Web abstract this publication describes an approach for the development of information security continuous. Web 805 in this template, the action plan includes.
Get Our Sample of Nist Security Assessment Plan Template Security
Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web planning and transition purposes, federal agencies may wish to closely follow the development of these new. Developing an iscm program assessment. Draft nist interagency report (nistir) 8212 , iscma: Web the fedramp poa&m template provides.
DFARS Archives CKSS Cybersecurity Solutions
Web after reviewing more than a year’s worth of community feedback, nist has released a draft of nist releases. Developing an iscm program assessment kelley. Draft nist interagency report (nistir) 8212 , iscma: Web on c&a activities what is continuous monitoring? Developing an iscm program assessment. Web abstract this publication describes an example methodology for.
NIST Risk Management Framework (RMF)
Draft nist interagency report (nistir) 8212 , iscma: Web planning and transition purposes, federal agencies may wish to closely follow the development of these new. Developing an iscm program assessment. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through. It was developed directly from nist guidance and is.
Nist Security Plan Template Template 1 Resume Examples MZe12Xo3jx
Web on c&a activities what is continuous monitoring? Web continuous monitoring programs facilitate ongoing awareness of threats, vulnerabilities, and information security to support. Developing an iscm program assessment kelley. Web after reviewing more than a year’s worth of community feedback, nist has released a draft of nist releases. Developing an iscm program assessment. Draft nist.
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
Web on c&a activities what is continuous monitoring? Nist information system contingency plan templates for high, moderate, and low. It was developed directly from nist guidance and is applicable to any organization,. Developing an iscm program assessment. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through. Web 805.
Nist Risk Management Framework Template Risk management, Project risk
Web abstract this publication describes an example methodology for assessing an organization's information. Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities,. Web on c&a activities what is continuous monitoring? Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy.
Nist Continuous Monitoring Plan Template Web abstract this publication describes an example methodology for assessing an organization's information. It was developed directly from nist guidance and is applicable to any organization,. Web on c&a activities what is continuous monitoring? Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and.
Developing An Iscm Program Assessment.
Web planning and transition purposes, federal agencies may wish to closely follow the development of these new. Developing an iscm program assessment kelley. Web the fedramp poa&m template provides a structured framework for aggregating system vulnerabilities and deficiencies through. Web october 01, 2020.
Web The Purpose Of This Guideline Is To Assist Organizations In The Development Of A Continuous Monitoring Strategy And.
Web continuous monitoring programs facilitate ongoing awareness of threats, vulnerabilities, and information security to support. Web abstract this publication describes an example methodology for assessing an organization’s information. Web nistir 8212, an information security continuous monitoring program assessment, provides an operational. It was developed directly from nist guidance and is applicable to any organization,.
Web Abstract This Publication Describes An Example Methodology For Assessing An Organization's Information.
Web after reviewing more than a year’s worth of community feedback, nist has released a draft of nist releases. Web 805 in this template, the action plan includes rows for the priority of each action item, a description 806 of the action. Web abstract this publication describes an approach for the development of information security continuous. Draft nist interagency report (nistir) 8212 , iscma:
Web Continuous Monitoring (Iscm) Program.
Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and. Nist information system contingency plan templates for high, moderate, and low. Web on c&a activities what is continuous monitoring? Web information security continuous monitoring (iscm) is defined as maintaining ongoing awareness of information security, vulnerabilities,.